Menu

Judicial separation is a legal process in which a married couple is formally recognized as living apart, but the marriage itself remains legally valid. It provides an alternative to divorce
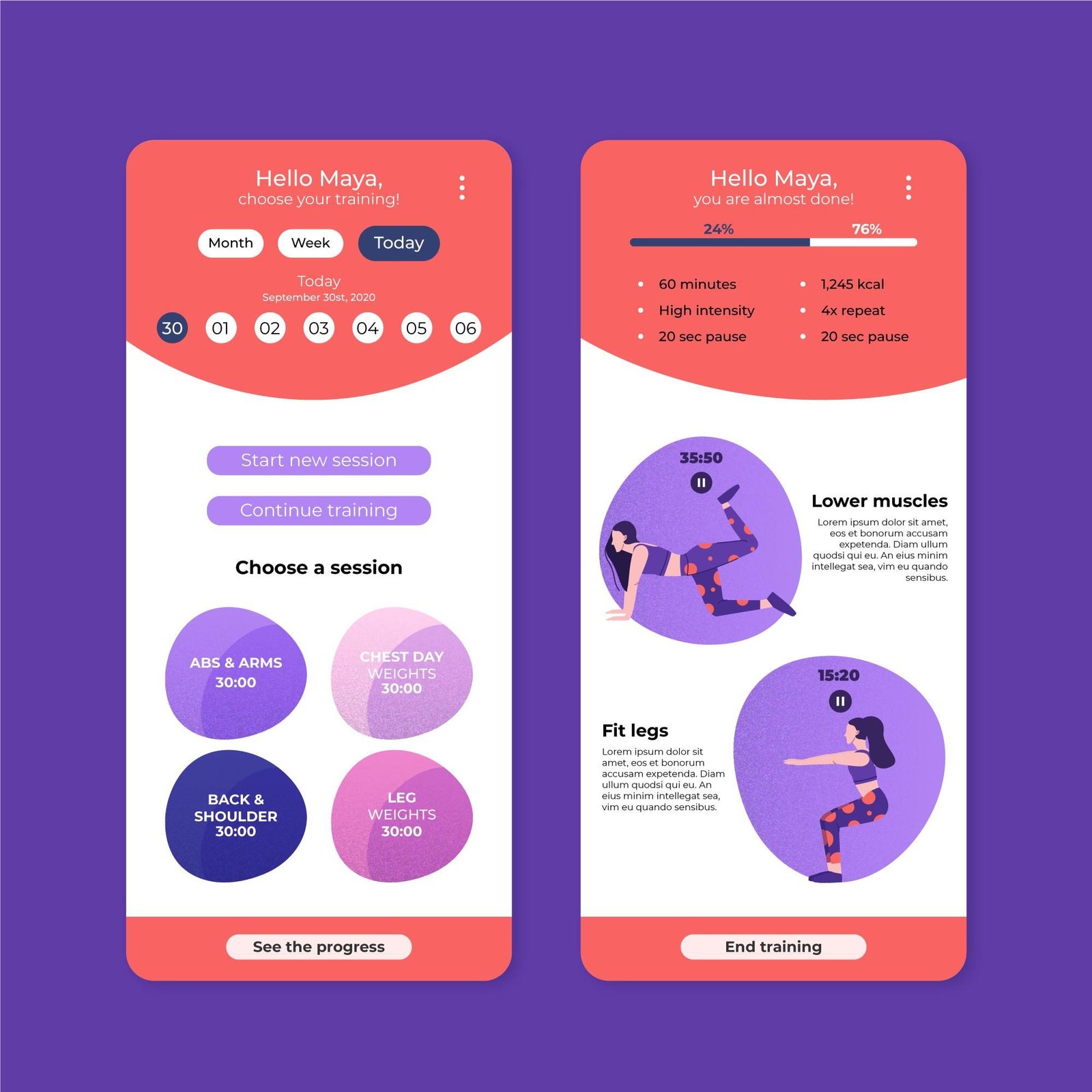
Mobile app design is at the intersection of creativity, functionality, and user experience, playing a crucial role in shaping how users interact with digital products. As the mobile app market

A partnership with a digital marketing company in Bangalore or a digital transformation company in India is not just an investment in services but in the future of your business.

Join Webkorps at CES in Las Vegas and explore cutting-edge digital transformation solutions, including custom software, AI, IoT, blockchain, and more. Transform your business today!

The digital landscape is evolving at an unprecedented pace, and at the heart of this transformation lies a groundbreaking technology: generative AI. Imagine machines that can create art, compose music, write stories, and even generate lifelike images—all on their own.
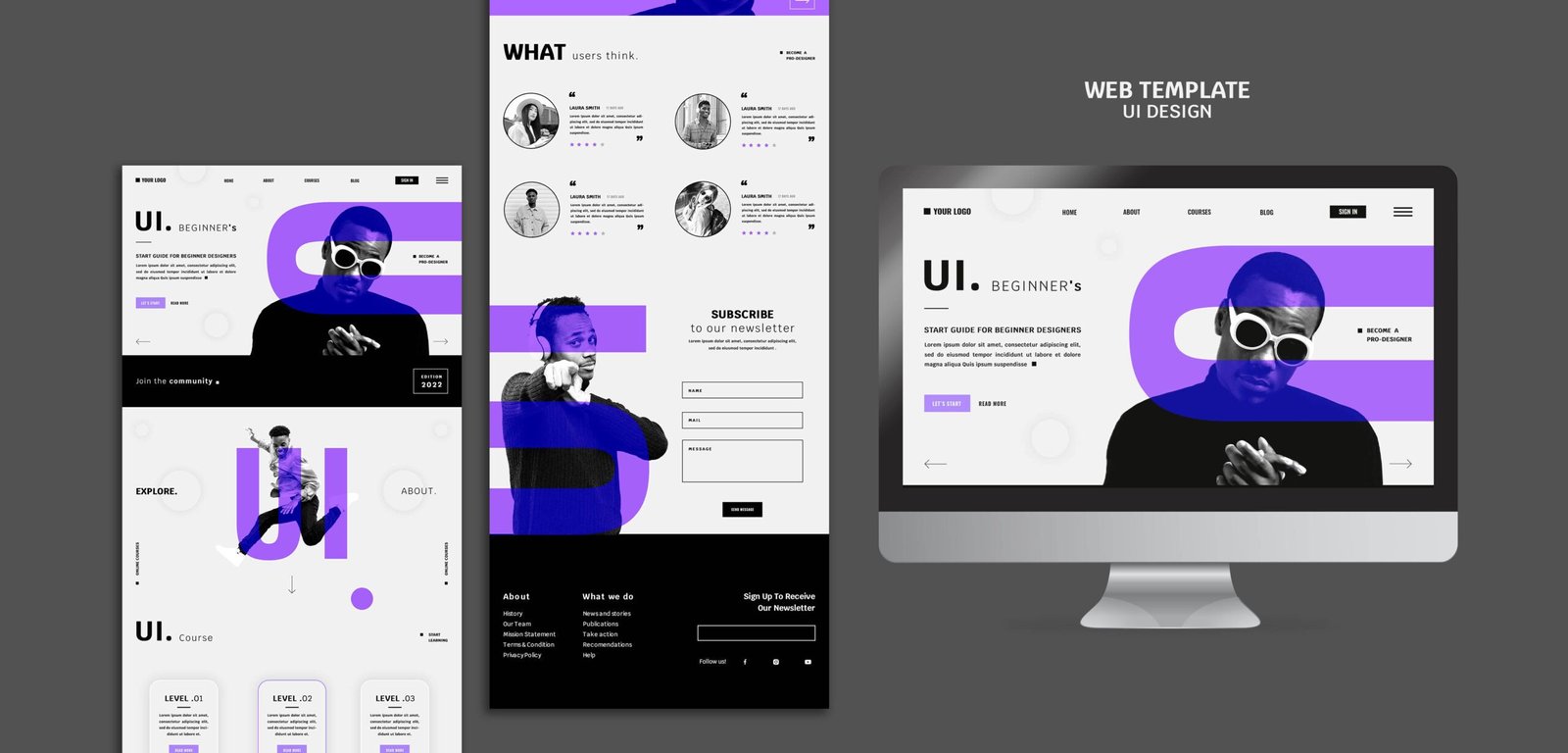
Mobile app design is the cornerstone of creating applications that not only look great but also provide seamless and engaging user experiences. With billions of mobile users worldwide, the demand
We hope this read was helpful to you! Don’t forget to follow Guest Genius Hub for more relevant and informative content!